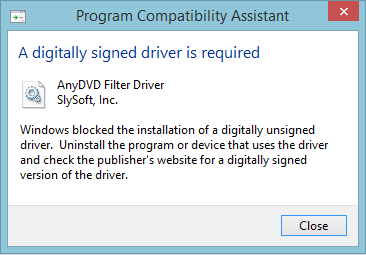
If the driver you are trying to install is not properly signed you will get the following screen:
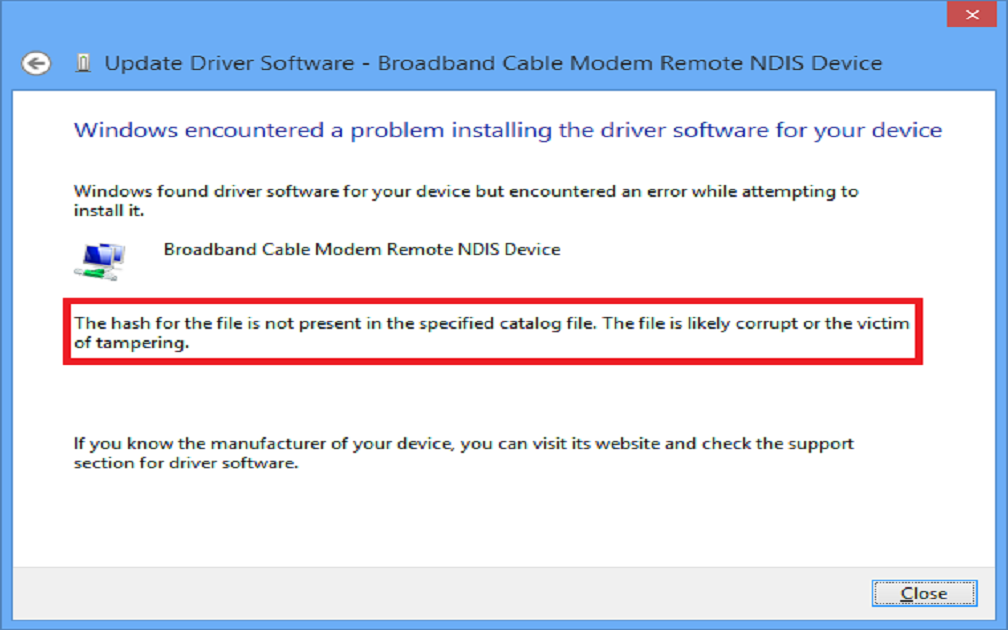
“Windows found driver software for your device but encountered an error while attempting to install it. The hash for the file is not present in the specified catalog file. The file is likely corrupt or the victim of tampering.”
If you are sure about the driver you are trying to install then you need to disable driver signature enforcement in Windows.
You can do this in 2 ways.