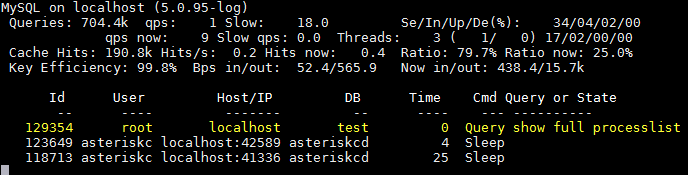
 MyTOP is an utility for tracking performance and connections to MySQL/MariDB servers. The interface is very similar to top utility. Further examples is performed in CentOS 6 x64 operating system.
MyTOP is an utility for tracking performance and connections to MySQL/MariDB servers. The interface is very similar to top utility. Further examples is performed in CentOS 6 x64 operating system.
First of all we need to plug Epel repository:
|
1 2 |
wget http://mirror.omnilance.com/epel/6/x86_64/epel-release-6-8.noarch.rpm rpm -Uvh epel-release-6-8.noarch.rpm |

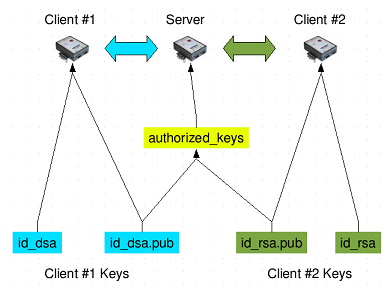 SSH keys provide a more secure way of logging into a virtual private server with SSH than using a password alone. While a password can eventually be cracked with a brute force attack, SSH keys are nearly impossible to decipher by brute force alone. Generating a key pair provides you with two long string of characters: a public and a private key. You can place the public key on any server, and then unlock it by connecting to it with a client that already has the private key. When the two match up, the system unlocks without the need for a password. You can increase security even more by protecting the private key with a passphrase.
SSH keys provide a more secure way of logging into a virtual private server with SSH than using a password alone. While a password can eventually be cracked with a brute force attack, SSH keys are nearly impossible to decipher by brute force alone. Generating a key pair provides you with two long string of characters: a public and a private key. You can place the public key on any server, and then unlock it by connecting to it with a client that already has the private key. When the two match up, the system unlocks without the need for a password. You can increase security even more by protecting the private key with a passphrase.  The thing I needed is an amazing Dropbox-Uploader script from Andrea Fabrizi be installed on my Asus RT-N14U router with Padavan’s firmware. Dropbox-Uploader needs Bash shell to run so i had to install it. I assume Entware is already enabled in your router in Advanced Settings –> USB Apllication –> Allow Run Optware? as on the screenshot below:
The thing I needed is an amazing Dropbox-Uploader script from Andrea Fabrizi be installed on my Asus RT-N14U router with Padavan’s firmware. Dropbox-Uploader needs Bash shell to run so i had to install it. I assume Entware is already enabled in your router in Advanced Settings –> USB Apllication –> Allow Run Optware? as on the screenshot below: