When attempting to connect or establish Remote Desktop connection to a remote Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1 or Windows 10 computer in order to remotely logon to the machine, the log on may be rejected with Remote Desktop client returns one of the following error messages:
Your credentials did not work.
or
Unable to log you on because of an account restriction.
or
An authentication error has occurred.
The Local Security Authority cannot be contactedRemote Computer: xxxxx
or
A user account restriction (for example, a time-of-day restriction) is preventing you from logging on. For assistance, contact your system administrator or technical support.
By default, Windows operating system does not allow nor permit user account without password set or user name with blank (null) password to connect and log in remotely via Remote Desktop Protocol (RDP).
The obvious resolution is definitely to create and set a password for the user account that requires to logon remotely to a computer via Remote Desktop, and it’s recommended for security reason too. However, user who for some reason such as for the purpose of convenient, and thus unable or cannot assign a password to the user account, can use the following workaround to allow user to login remotely via Remote Desktop Connection (RDP) client to Windows PC.
ImportantThe configuration to enable null (blank) passwords logon must be done on the host computer, i.e. the remote computer to remotely controlled.
How to Enable Remote Login via Blank Passwords using Local Security Policy or Group Policy Editor
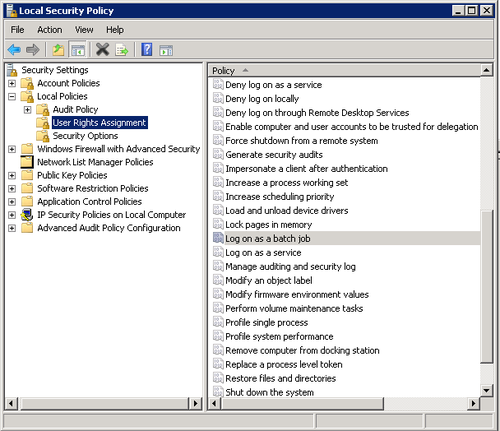
- To configure the Remote Desktop host computer to accept user name with blank password, go to Control Panel -> Administrative Tools (Under System and Maintenance in Windows Vista / Windows 7 / Windows 8 / Windows 8.1 and Windows 10) -> Local Security Policy.Alternatively, run GPEdit.msc (Group Policy Editor).
- For Local Security Policy, expand Security Policies / Security Settings-> Local Securities / Local Policies -> Security Options.For Group Policy Editor or GPEdit.msc, expand Local Computer Policy -> Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options.
- Locate Accounts: Limit local account use of blank passwords to console logon only policy, and set its value to Disabled.
Once disabled, user account with blank or null passwords can now login remotely via Remote Desktop Connection client instead of just able to do so via local console.
How to Configure Blank Passwords Allowed for Remote Log On via Registry
Windows stores the value of the policy set above in a registry key named “LimitBlankPasswordUse”. To unlock the limitation of cannot establish Remote Desktop logon with user account without a password, simply set the value data for LimitBlankPasswordUse to 0 (so that there is no limit on blank or null password use), as according to the code below. Alternatively, copy and paste the following text to a text file, and save with a .reg extension. Then run the .reg file to merge the value to registry.
|
1 2 3 4 5 6 7 |
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Lsa] "LimitBlankPasswordUse"=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa] "LimitBlankPasswordUse"=dword:00000000 |
For convenient, two registry files have been created and available for free download, which will enable or disable usage of blank password (or absent of password) to login remotely. Download BlankPasswords.zip (no longer available) and run EnableBlankPasswords.reg to enable or DisableBlankPasswords.reg to disable remote login via blank password.
This works on both 32-bit and 64-bit Windows operating systems.