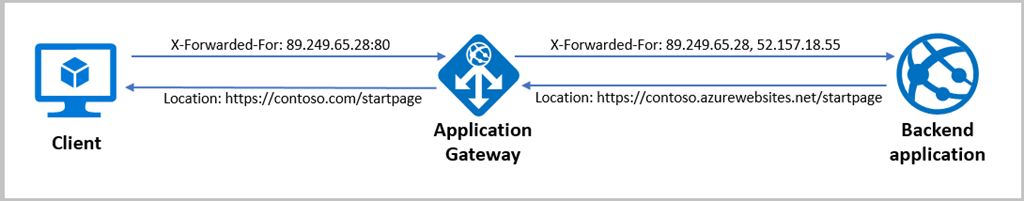
 If your Azure App Service is behind Azure Application Gateway you will need to implement Strict Transport Security and Secure Headers in your Azure Application Gateway instead of App Service’s web.config or .htaccess
If your Azure App Service is behind Azure Application Gateway you will need to implement Strict Transport Security and Secure Headers in your Azure Application Gateway instead of App Service’s web.config or .htaccess
Azure Application Gateway has an ability to add, remove or modify inbound and outbound headers. This can be done in “Rewrites” section of your Application Gateway’s blade.
Click “+ Rewrite set”
In the first step of the Wizard name the rewrite set and choose routing rules and paths to apply this set to and click “Next”.
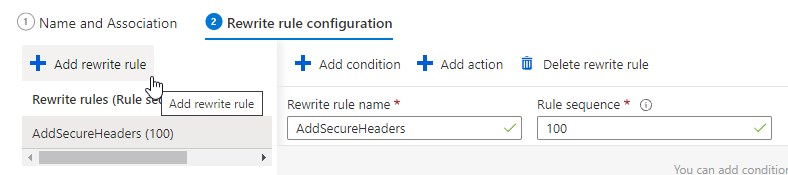
Now click on “Add rewrite rule” and name the rule for example “AddSecureHeaders”:
 Next, click on “Add action”. You will see the new action entry appeared in the pane:
Next, click on “Add action”. You will see the new action entry appeared in the pane:
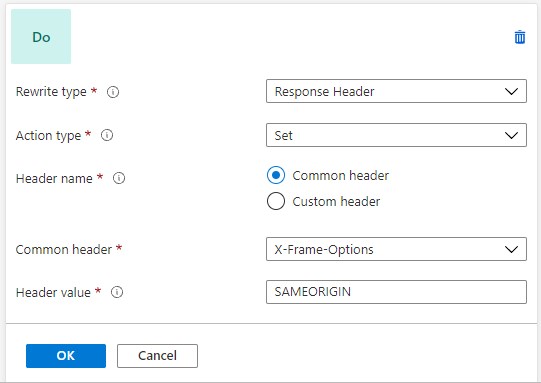
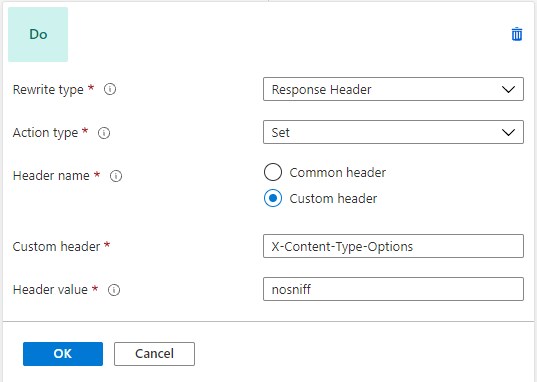
 Click on it and it will expand with a menu where you can set properties of the new header for you want to add. In “Rewrite type” choose “Response Header” and in “Action Type” choose “Set”.
Click on it and it will expand with a menu where you can set properties of the new header for you want to add. In “Rewrite type” choose “Response Header” and in “Action Type” choose “Set”.
If your “Header name” type as “Common header” you will be able to choose a header from a predefined list. In case of “Custom header” you will be able to set header’s name manually.
Here is an example of X-Frame-Options header configured in Azure Application Gateway:
 Click OK and “Add action” to add another header. Let’s say this time it will be Custom header X-Content-Type-Options:
Click OK and “Add action” to add another header. Let’s say this time it will be Custom header X-Content-Type-Options:
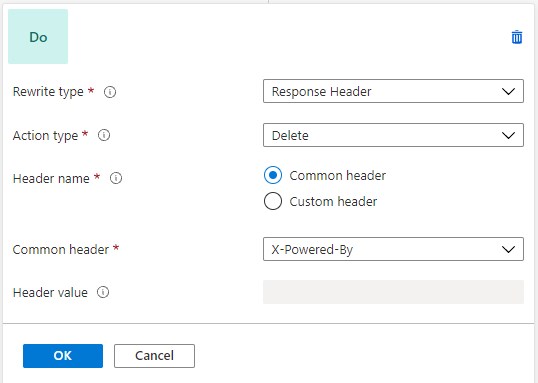
 If we want to remove unnecessary headers such as “Server” or “X-Powered-By“, we choose “Action type” – “Delete”. Here is an example:
If we want to remove unnecessary headers such as “Server” or “X-Powered-By“, we choose “Action type” – “Delete”. Here is an example:
Here is a complete list of rules:
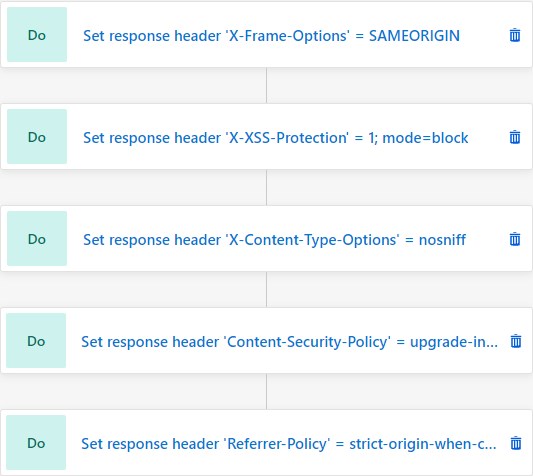
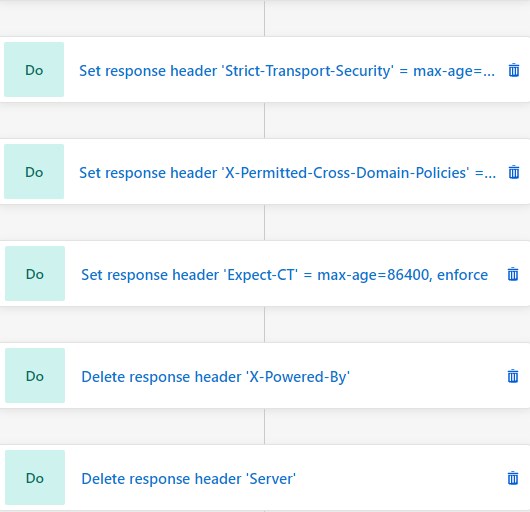
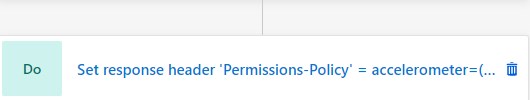 For your convenience here is a text representation of the rules above in IIS
For your convenience here is a text representation of the rules above in IIS web.config file with the comments for each rule. Just copy values from the file’s example :
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 |
<?xml version="1.0" encoding="UTF-8"?> <configuration> <system.web> <httpRuntime enableVersionHeader="false" /> <!-- Removes ASP.NET version header. --> </system.web> <system.webServer> <security> <requestFiltering removeServerHeader="true" /> <!-- Removes Server header in IIS10 or later and also in Azure Web Apps --> </security> <httpProtocol> <customHeaders> <clear /> <!-- Gets rid of the other unwanted headers --> <add name="X-Frame-Options" value="SAMEORIGIN"/> <!-- disables iframing the website from other than the origin --> <add name="X-Xss-Protection" value="1; mode=block"/> <!-- configure the built in reflective XSS protection found in Internet Explorer, Chrome and Safari (Webkit). --> <add name="X-Content-Type-Options" value="nosniff"/> <!-- prevents Google Chrome and Internet Explorer from trying to mime-sniff the content-type of a response away from the one being declared by the server --> <add name="Content-Security-Policy" value="upgrade-insecure-requests; base-uri 'self'; frame-ancestors 'self'; form-action 'self'; object-src 'none';"/> <!-- It is a complex policy of what can execute. This can be really restrictive so please read up on it if you tighten it. I have laid out basic setting that is very permissive and will not save you from XSS attacks. https://content-security-policy.com/ or https://infosec.mozilla.org/guidelines/web_security#content-security-policy --> <add name="Referrer-Policy" value="strict-origin-when-cross-origin"/> <!-- https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Referrer-Policy - Sets the referrer policy. Use for CORS --> <add name="Strict-Transport-Security" value="max-age=31536000; includeSubDomains; preload"/> <!-- https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Strict-Transport-Security - HSTS allows you to tell a browser that you always want a user to connect using HTTPS instead of HTTP. his policy will enforce TLS on your site and all subdomains for a year. --> <add name="Permissions-Policy" value="accelerometer=(self), camera=(self), geolocation=(self), gyroscope=(self), magnetometer=(self), microphone=(self), payment=(self), usb=(self)" /> <!-- used to disable certain features https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Feature-Policy --> <add name="X-Permitted-Cross-Domain-Policies" value="none"/> <!-- The X-Permitted-Cross-Domain-Policies header tells clients like Flash and Acrobat what cross-domain policies they can use. If you don’t want them to load data from your domain, set the header’s value to none --> <add name="Expect-CT" value="max-age=86400, enforce"/> <!-- The Expect-CT header allows sites to opt in to reporting and/or enforcement of Certificate Transparency requirements, which prevents the use of misissued certificates for that site from going unnoticed. --> <remove name="X-Powered-By" /> <!-- removes the X-Powered-By:ASP.NET header --> </customHeaders> <redirectHeaders> <clear /> </redirectHeaders> </httpProtocol> </system.webServer> </configuration> |
After finishing creating the rules don’t forget to click blue “Create” button in the lower left corner.
Now check your website through a tool like https://securityheaders.com/ and you will see what is it that your website is missing from the best practices.
That’s it! Good luck!