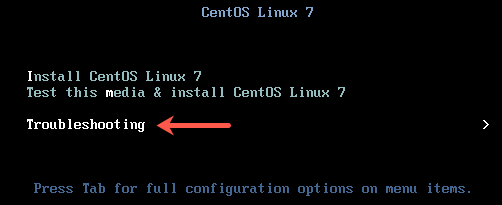
 A situation where the system has no kernel to boot from maybe because all the kernel are removed from the system or due to a corruption, Kernel installation from rescue mode is required. You can still install a new kernel from rescue mode and make the system up and be running again. Continue reading
A situation where the system has no kernel to boot from maybe because all the kernel are removed from the system or due to a corruption, Kernel installation from rescue mode is required. You can still install a new kernel from rescue mode and make the system up and be running again. Continue reading
May 07 2020
CentOS / RHEL 7 : How to install kernel from rescue mode
May 06 2020
Inspecting and extracting Debian package contents
This post covers how to list and extract the contents of a Debian package. There will be examples used to show how to list the contents of debian packages that are installed and not-installed on a system, as well as, how to extract the debian control information and program files.
A debian package is a Unix ar archive that includes two tar archives: one containing the control information and another with the program data to be installed. Continue reading
May 06 2020
Inspecting and extracting RPM package contents
This article will cover basics of the RPM package architecture and show how we can see RPM package content and extract it. There will be examples how to extract RPM package files from Linux command line.
An RPM package is simply a header structure on top of a CPIO archive. The package itself is comprised of four sections: a header with a leading identifier (magic number) that identifies the file as an RPM package, a signature to verify the integrity of the package, the header or ‘tagged’ data containing package information, version numbers, and copyright messaging, and the archive containing the actual program files.
Apr 27 2020
Recover WSFC and AlwaysOn from Resolving State
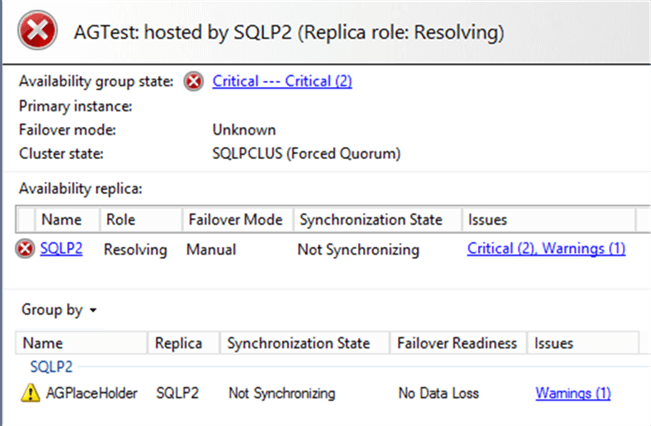 There is a SQL Server Availability Group (AG) on a Windows Server Failover Cluster (WSFC) with 3 nodes using Node Majority quorum configuration. In an unforeseen circumstance, 2 nodes went completely offline at the same time causing the WSFC to go down.
There is a SQL Server Availability Group (AG) on a Windows Server Failover Cluster (WSFC) with 3 nodes using Node Majority quorum configuration. In an unforeseen circumstance, 2 nodes went completely offline at the same time causing the WSFC to go down.
This caused the Availability Group to go into a Resolving state and all the databases in the AG and the AG Listener to be inaccessible. How to recover the WSFC cluster node to start without a quorum and later fully re-establish HA for AlwaysOn AG I’ll show below. Continue reading
Apr 22 2020
Disable send_redirects or NETKEY
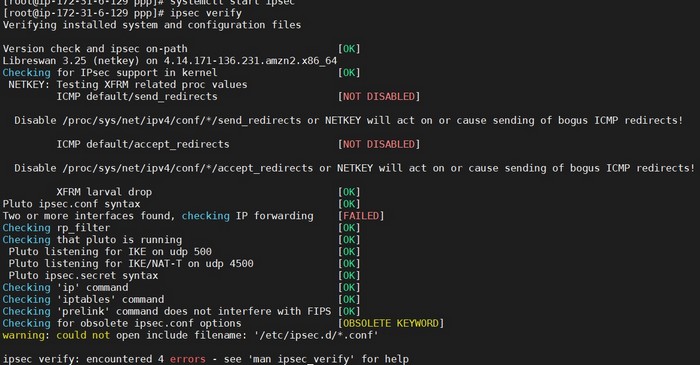 During the process of a VPN client configuration with xl2tpd and openswan
During the process of a VPN client configuration with xl2tpd and openswan ipsec verify command threw the following error:
Disable /proc/sys/net/ipv4/conf/*/send_redirects or NETKEY will act on or cause sending of bogus ICMP redirects!
To fix this we need to disable send_redirects and save changes in /etc/sysctl.conf so they will be permanent across reboots. Here is how: Continue reading
Apr 21 2020
Asterisk responds with 404 Not Found
 While configuring SIP/PJSIP in Asterisk you may notice that Asterisk responds with 404 Not Found to the OPTIONS request. To demonstrate the behavior let’s have a look at this PJSIP debug log example: Continue reading
While configuring SIP/PJSIP in Asterisk you may notice that Asterisk responds with 404 Not Found to the OPTIONS request. To demonstrate the behavior let’s have a look at this PJSIP debug log example: Continue reading
Apr 20 2020
Windows Allow Remote Desktop Login Without Password
When attempting to connect or establish Remote Desktop connection to a remote Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1 or Windows 10 computer in order to remotely logon to the machine, the log on may be rejected with Remote Desktop client returns one of the following error messages: Continue reading
Mar 24 2020
How To Enable CentOS 8 PowerTools Repo
The CentOS 8 PowerTools repo may be required for some packages in the EPEL Repo. Below are instructions on how to enable PowerTools repo in CentOS 8. Continue reading
Mar 24 2020
How To Install and Enable EPEL Repo on CentOS 8
You can easily install various packages by configuring a CentOS 8 system to use Fedora EPEL repos and third party packages. This quick tutorial explains how to configure a CentOS Linux version 8.x to use the Fedora Extra Packages for Enterprise Linux (EPEL) repository. Continue reading
Mar 21 2020
IIS Redirect HTTP to HTTPS
Once the SSL certificate is installed, your site still remains accessible via a regular insecure HTTP connection. To connect securely, visitors must specify the https:// prefix manually when entering your site’s address in their browsers.
In order to force a secure connection on your website, it is necessary to set up HTTP to HTTPS redirection rule in IIS. This way, anyone who enters your site using a link like “yourdomain.com” will be redirected to “https://yourdomain.com” or “https://www.yourdomain.com” (depending on your choice) making the traffic encrypted between the server and the client side. Continue reading




