
I can bet that 9 of 10 smartphone owners use some text messenger to chat with family and friends. You must be too… Have you heard about Signal messenger? If you take care seriously about your privacy I can bet you do heard or use it already! If not – maybe it’s a right time to start! I’m not going to prove again here that keeping your identity private in Internet must be a part of your life philosophy. All I want to remind now is: you are never know what information and when will be used against you. Continue reading



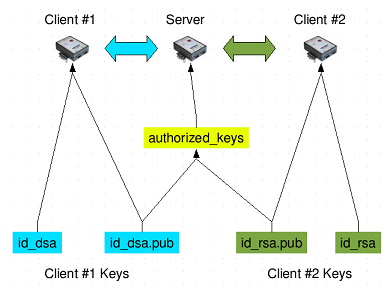 SSH keys provide a more secure way of logging into a virtual private server with SSH than using a password alone. While a password can eventually be cracked with a brute force attack, SSH keys are nearly impossible to decipher by brute force alone. Generating a key pair provides you with two long string of characters: a public and a private key. You can place the public key on any server, and then unlock it by connecting to it with a client that already has the private key. When the two match up, the system unlocks without the need for a password. You can increase security even more by protecting the private key with a passphrase.
SSH keys provide a more secure way of logging into a virtual private server with SSH than using a password alone. While a password can eventually be cracked with a brute force attack, SSH keys are nearly impossible to decipher by brute force alone. Generating a key pair provides you with two long string of characters: a public and a private key. You can place the public key on any server, and then unlock it by connecting to it with a client that already has the private key. When the two match up, the system unlocks without the need for a password. You can increase security even more by protecting the private key with a passphrase.  The thing I needed is an amazing Dropbox-Uploader script from Andrea Fabrizi be installed on my Asus RT-N14U router with Padavan’s firmware. Dropbox-Uploader needs Bash shell to run so i had to install it. I assume Entware is already enabled in your router in Advanced Settings –> USB Apllication –> Allow Run Optware? as on the screenshot below:
The thing I needed is an amazing Dropbox-Uploader script from Andrea Fabrizi be installed on my Asus RT-N14U router with Padavan’s firmware. Dropbox-Uploader needs Bash shell to run so i had to install it. I assume Entware is already enabled in your router in Advanced Settings –> USB Apllication –> Allow Run Optware? as on the screenshot below:


