When you need to find out your DB users and their permissions on DB objects use the following query to list all MS SQL users and their permissions on databases and views and get a report: Continue reading
Dec 15 2023
Flash Operator Panel 2 Connecting to server error
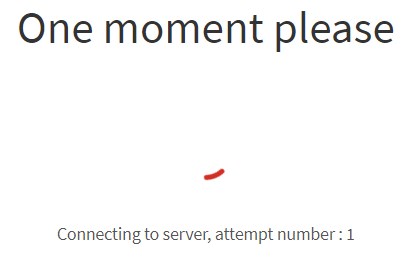 The case when FOP2 with HTTPS does not work and you can see “Connecting to server, attempt number ” message was described here
The case when FOP2 with HTTPS does not work and you can see “Connecting to server, attempt number ” message was described here
Another case when this error can happen is when you try to log in as an operator and access /fop2 path
Nov 24 2023
ViciBox 11 installation in Cloudmin
 ViciBox is worldwide popular callcenter solution. If you want to run ViciBox in virtual machine under Cloudmin you will need to perform a few additional steps to make running because there is no ready-to-go ViciBox image for Cloudmin available. Continue reading
ViciBox is worldwide popular callcenter solution. If you want to run ViciBox in virtual machine under Cloudmin you will need to perform a few additional steps to make running because there is no ready-to-go ViciBox image for Cloudmin available. Continue reading
Nov 22 2023
Difference between BACPAC and DACPAC
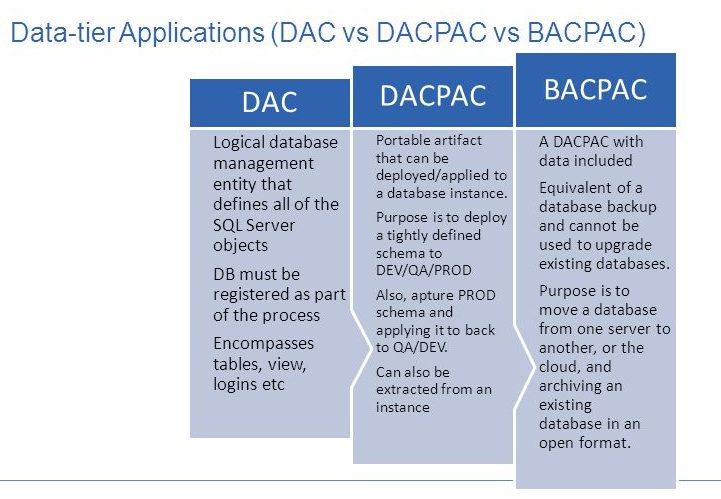
A data-tier application (DAC) is a self-contained unit of MS SQL Server database deployment that allows packing SQL Server objects into a portable artifact called a DAC package. It is also known as a DACPAC.
BACPAC is simple to export a SQL Server database which will eventually require import to another server or even for longer-term retention.
IN SHORT:
A BACPAC includes the schema and data from the database.
DACPAC has only the schema and not the data.
Now we will see the difference between BACPAC and DACPAC Continue reading
Aug 19 2023
Vicidial: How to update phones Server IP in bulk
To simultaneously update Server IP for all phones in ViCiDial, please log in to your MySQL (or PhpMyAdmin, if available) and run the following SQL statements:
|
1 |
update phones set server_ip ='1.1.1.1'; |
where instead of “1.1.1.1” specify your Vicidial Server IP.
Check also How to update passwords in bulk in ViciDial
Aug 09 2023
postfix/submission/smtpd certificate expired alert number 45
I tried to configure Laravel mail client with secure connection via TLS to my email server but in email client I got:
Unable to connect with STARTTLS: stream_socket_enable_crypto(): SSL operation failed with code 1. OpenSSL Error messages: error:14090086:SSL routines:ssl3_get_server_certificate:certificate verify failed.
At the same time on my email server in /var/log/maillog I observed the following:
Aug 8 10:05:46 mail postfix/submission/smtpd[30830]: connect from unknown[111.211.48.11]
Aug 8 10:05:46 mail postfix/submission/smtpd[30830]: SSL_accept error from unknown[111.211.48.11]: 0
Aug 8 10:05:46 mail postfix/submission/smtpd[30830]: warning: TLS library problem: 30830:error:14094415:SSL routines:ssl3_read_bytes:sslv3 alert certificate expired:s3_pkt.c:1493:SSL alert number 45:
Aug 8 10:05:46 mail postfix/submission/smtpd[30830]: lost connection after STARTTLS from unknown[111.211.48.11]
Aug 8 10:05:46 mail postfix/submission/smtpd[30830]: disconnect from unknown[111.211.48.11]
But Letsencrypt certificate was up to date. Continue reading
Jun 16 2023
How to create full-chain pem certificate
You can use your favourite text editor to create a combined full-chain pem certificate. The most important here is the order.
The correct order in a .crt file will be the following: Continue reading
Jun 16 2023
How to create full-chain pfx certificate
Full-chain pfx certificate can be created by the one of the following methods
Continue reading
Jun 16 2023
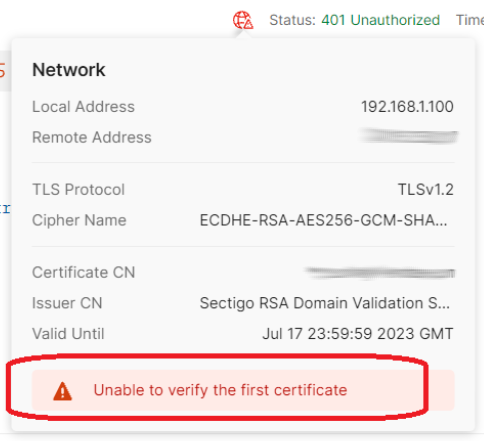
Postman Unable to verify the first certificate
The error Unable to verify the first certificate occurs in Postman cloud agent because it does not have Trusted Root certificates storage with intermediate and root CA certificates thus cannot verify client → intermediate → root CA chain. Azure Application Gateway does not have Trusted Root certificates storage as well so the error occurs under these conditions. Continue reading
May 19 2023
HAProxy mixed content warning when using HTTPS
 I use HAProxy to do SSL offloading for a WordPress site. Frontend is on 80 and 443 with redirect HAProxy redirect HTTP to HTTPS using
I use HAProxy to do SSL offloading for a WordPress site. Frontend is on 80 and 443 with redirect HAProxy redirect HTTP to HTTPS using
redirect scheme https code 301 if !{ ssl_fc }
Redirection is working well when the page is accessed on port 80.
However the pages loads incomplete and looking in the console of Firefox/Chrome it can be seen that “mixed mode content” is blocked by the browser. Some stylesheets, scripts an images are still accessed over http instead of https.
301 is permanent redirection, so why is this happening? The browser should not even try http because it should be aware of the permanent redirection. And besides that, even when http is used accidentally, it should still be redirect to https instead. Continue reading